Click to learn more about author Samuel Bocetta.
Cyberattacks can affect organizations of any size and at any time. The FBI estimates ransomware costs companies about $1 billion annually, which makes it one of the most damaging viruses around.
Say you are a customer service representative for a small online retail store. If your workstation becomes infected with a ransomware virus, your screen may be taken over by the hackers with a message about demands for payment. Meanwhile, the malware begins encrypting your entire hard drive to make the files inaccessible.
How do you avoid getting into this kind of mess? Education, dear reader. The following discussion will help get you up to speed on the best tips for protecting yourself against ransomware.
Watch for Social Engineering
What makes ransomware so dangerous is that it only takes a single point of failure in your organization to launch an attack. As an employee of an online retailer, you could accidentally give a hacker access to your computer, which could lead to spreading malware across the network and putting the entire company in jeopardy.
Ransomware viruses typically propagate through social engineering attacks, especially email phishing. You may receive a personalized message from an unknown sender claiming that there is a problem with one of your online accounts. The email will either include a malicious attachment or direct you to click on a suspicious link.
If you perform one of these actions, the hacker may be able to infiltrate your computer and seize control. At that point they will launch an installer to load the ransomware virus and block all other activities on your screen. To avoid this situation, it’s best to block or delete mail that comes from unknown senders.
Keep Systems Up to Date
New instances of ransomware viruses are constantly popping up all over the internet, and as a result, developers of operating systems and antivirus software have the difficult task of trying to stay ahead of the trends. As a user or IT professional, the best thing you can do is set up your computer to check for software updates on a regular basis with automatic installation.
Microsoft Windows is the operating system most often targeted by hackers, but be aware that ransomware attacks can be executed on Mac OS, Linux, and even smartphones or tablets. For any device that you plan to connect to your organization’s network, be sure it has all patches installed and a virus scan tool with the latest definition updates.
Invest in Security Solutions
At an organizational level, your IT security team can leverage modern solutions to help combat potential ransomware attacks. For example, the software company Splunk now offers a special Analytics Tool that monitors activity on your local network and proactively warns you if a hack is imminent.
Of course, these types of security systems still need a certain level of human interaction in order to properly assess a threat and make decisions about how to react. But by joining human abilities with Machine Learning and Artificial Intelligence, you can stay ahead of hackers and reduce the risk of an attack.
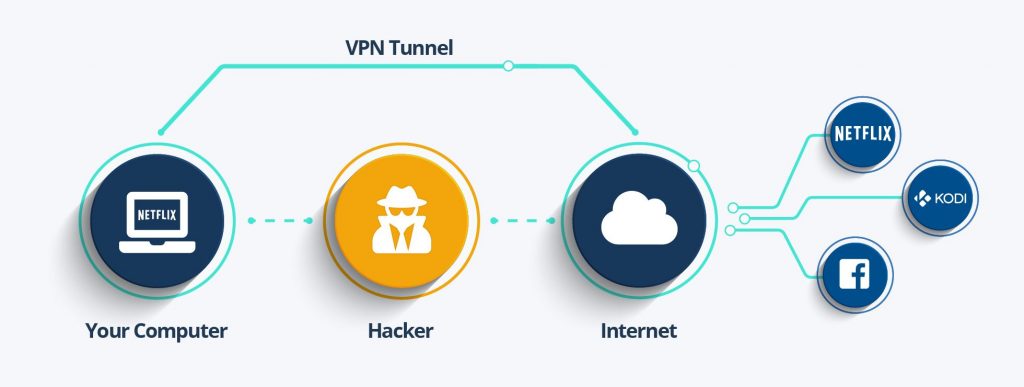
Use a Trusted VPN Client
Modern companies need to be flexible and it’s more commonplace for staff to work from remote locations, not just in an office with a secured network. But going offsite poses a risk when it comes to cybersecurity, because letting devices connect to external networks means they are more exposed to hacks, secret penetrations of a sometimes official variety, and viruses.
In order to lock down internal databases and resources as much as possible, all computers and mobile devices should be required to have a virtual private network (VPN) client. VPNs offer secure encryption between a piece of hardware and the open internet, which prevents hackers from being able to hijack a session or intercept network traffic.
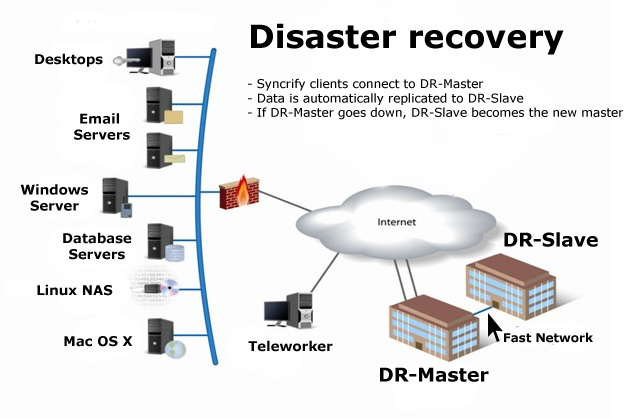
Have a Disaster Recovery Plan
You can never completely remove the risk of a ransomware attack, and as a result your organization needs to be prepared for the chance that one could affect your systems or hardware. There should be a dedicated disaster recovery team, including members from IT and other parts of the business, who maintain a plan for how to respond to a malware incident.
The first step in recovering from a ransomware attack is to disconnect the affected machine from the local network, otherwise you run the chance of the virus spreading to more devices.
Then you need to weigh your options. It’s not advised for you to contact the hacker or submit the ransom payment, because there is a low likelihood that they will actually remove the virus or decrypt your files.
Instead, wipe the affected hard drive as soon as possible and load a backup copy from an secure, encrypted environment.
Emphasize Security Training
If members of the organization are not informed about how ransomware attacks work and spread, then it increases the risk of a hack occurring. Mandatory training sessions should be held on a regular basis, quarterly if possible, where individuals learn about cybersecurity trends and the dangers to look for when online. Ransomware should be a topic of emphasis, including examples of recent attacks in the news and how they started and spread.
Final Thought
Here’s a sneaky drill you might choose to conduct. It’s the internet version of the scared straight idea that judges sometimes use to keep juvenile delinquents from becoming adult prison lifers.
It goes like this.
Launch an unannounced internal test in which you pose as a hacker and try to execute a phishing attack over email or instant message. The manner in which your staff reacts could give you a very clear idea about how effective the security training and procedures are.
Just remember not to become inconsolably depressed or immediately fire the entire workforce if they underperform. Keep the larger point in mind to use it as a teaching tool, not a mechanism for mass layoffs. Good luck and thanks for reading.
Image Credits: Samuel Bocetta