
Click to learn more about author Gilad David Maayan.
Is your development process producing secure software? Ensuring that their software is secure is one of the main challenges developers face daily. It is not enough to test the software only at the required stages, which can result in overlooking minor vulnerabilities. The attackers are always ready to exploit even the slightest flaw.
One of the key strategies you can use to secure your software is a Secure Software Development Lifecycle (Secure SDLC or SDL). Read on to learn about the SDL, why it is important, and how you can implement it.
What Is Secure SDLC and Why Is Important for You?
Secure Development Lifecycle (SDL) is the process of including security artifacts in the Software Development Lifecycle (SDLC). SDLC, in turn, consists of a detailed plan that defines the process organizations use to build an application from inception until decommission.
Development teams use different models such as Waterfall, Iterative or Agile. However, all models usually follow these phases:
- Planning and requirements
- Architecture and design
- Test planning
- Coding
- Testing the code and results
- Release and maintenance

Developers usually performed security-related tasks only at the testing stage, resulting in discovering issues too late or not at all. With time, teams started to integrate security activities to catch vulnerabilities early in the development cycle.
With this in mind, the concept of secure SDLC started. Secure SDLC integrates activities such as penetration testing, code review, and architecture analysis into all steps of the development process.
The main benefits of adopting a secure SDLC include:
- Makes security a continuous concern—including all stakeholders in the security considerations
- Helps detect flaws early in the development process—reducing business risks for the organization
- Reduces costs—by detecting and resolving issues early in the lifecycle.
How Does Secure SDLC work?
Most companies will implement a secure SDLC simply by adding security-related activities to their development process already in place. For example, they can perform an architecture risk analysis during the design phase.
There are seven phases in most SDLCs although they may vary according to the methodology used, such as Agile or Waterfall:
- Concept
- Planning
- Design and Development
- Testing
- Release
- Sustain
- Disposal
For example, a development team implementing the waterfall methodology may follow the following scheme:
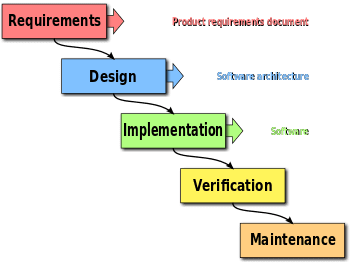
Each security activity should correspond with a phase in the SDLC, as follows:
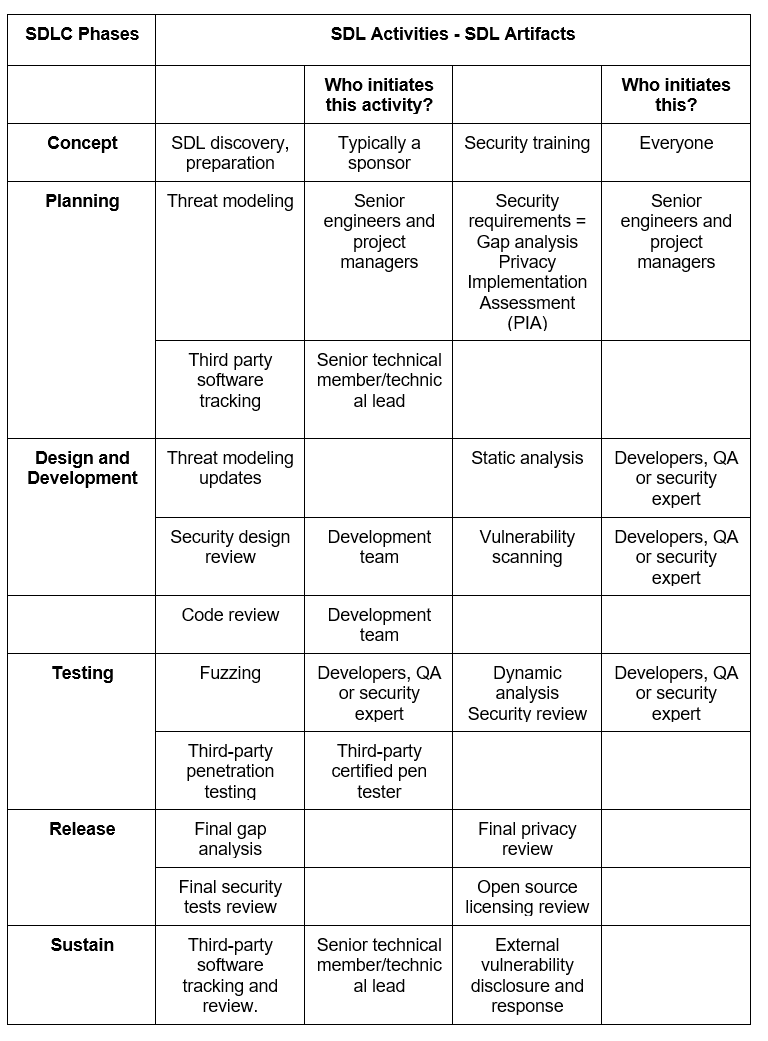
Some considerations to take into account when implementing a Secure SDLC are:
SDL Discovery
The goal should be to determine the security objectives required by the software, what are the possible threats and what regulations the organization needs to follow.
When working on the scope of the SDL, a development team should focus on deliverables such as security milestones, required certifications, risk assessments, key security resources, and required third-party resources.
Security Baselines
Here you should list what are the requirements your product need to comply with. For example, only using approved cryptography and libraries or using multifactor authentication. A Gap Analysis, contrasting the product’s features against the baseline, is useful to identify the areas not complying with the security baseline. When finding a gap, this needs to be addressed as early as possible in the lifecycle. Since companies release a product based on the percentage of compliance with the baseline, is important to work on gaps through the development process.
Security Training and Awareness
The company should provide security training sessions for developers, designers, architects, and QA. They can focus on secure design principles, security issues, web security or encryption.
Security awareness sessions are not geared specifically for the development team, involving everyone that is connected to the project within the organization. Sessions should be easy in terms of technical level and can include topics such as the various cybersecurity threats or risk impact and management.
Threat Modeling
Modeling the software components to identify and manage threats early in the development lifecycle. This helps the team to develop an incident response plan from the beginning, planing the appropriate mitigations early before the damage becomes more complicated to manage. Typically follows four steps, preparation, analysis, determine mitigations and validation. This activity can have different approaches such as protecting specific critical processes, exploit weaknesses or focus on the system design.
Third-Party Software Tracking
Since third-party software can be open source or commercial use, the team needs to list all third-party tools used in the project. This inventory should be done in the early stages of the development cycle. There are software tools that track and list the third-party components, sending you an alert if any component needs upgrading or has licensing issues.
Security Design and Peer Review
The development team should ensure the software is built with the most secure features. When reviewing the functional feature design, the developer should include a security design review, thinking like an attacker to discover the feature vulnerabilities. When reviewing the code, developers need to be aware of the most common coding security pitfalls. They can follow a checklist for secure coding, for example, that ensures that important security events are logged, check the permeability of the authentication process, or validate the user input.
Security Testing
While code review focus on functionality, security testing checks how vulnerable is the new product to attacks. Some of the testing activities include:
- Static Analysis—identifies the exact location of weaknesses by analyzing the software without executing it.
- Dynamic Analysis—identifies weaknesses by running the software, helping find infrastructure flaws and patch errors.
- Vulnerability Scanning—injects malicious inputs against running software to check how the program reacts. Mostly used to scan applications with a web interface.
- Fuzzing—involves giving invalid, random data to a program, to check for access protocols and file formats. The test helps find bugs that humans often miss by generating random input and try all possible variations.
- Third-party penetration testing—the tester simulates an attack to discover coding or system configuration flaws, and discover vulnerabilities a real attacker can exploit. It is required that the tester is an external party not connected to the team.
Data Disposal and Retention
Usually at the end of a product’s life companies dispose of old products, or data that they don’t need to use anymore. Many companies delete or overwrite encryption keys, in a process called “crypto-shredding”. While getting rid of outdated data is a necessity, there are concerns when comes to keep the confidentiality of the information. Some regulations such as GDPR have specific requirements for data disposal and retention.
What’s Next?
Implementing secure SDL helps you follow security best practices, integrating security activities and checkups across the development cycle. This will help to increase your product and company security posture.
